Protect Google Workspace (G-Suite)
AuthN by IDEE Integration: Google Workspace
Protect Everything
Google Workspace (G-Suite) is one of the most widely used cloud-based collaboration suites for business. It's where an organization will go to meet, create, & collaborate, and it must be protected. AuthN by IDEE integrates with Google Workspace harmoniously, to provide an extra layer of bullet-proof security, so tough it will eliminate all credential phishing and password-based attacks (including Adversary in the Middle AiTM). And so elegant, users will barely notice!
.avif)
Login You’ll Barely Notice
With AuthN same-device MFA, your new login and authentication flow is smoother than Sean Connery’s James Bond! In fact, it is so discrete, that you’ll barely notice it.
Users still visit the same URL, but they will be redirected to AuthN for login.
Then they are asked to unlock their device (however they usually do this, such as facial recognition, PIN, Windows Hello, Touch ID, or whatever it might be)!
As soon as the user has unlocked his or her device, they have authenticated and logged in.
Simple Integration in
Just a Few Steps
The great news is, it only takes a short time to set up your Google Workspace integration to keep your suite secured and 100% phish-proof right away. Google Workspace supports both SAML-based and OIDC-based SSO protocols – and so do we! Your organizations’ needs will help determine which configuration options you should select, however the most common way to connect is via SAML.
Step-by-Step Configuration Guide
You’ll need to login to the integrations portal and then follow these simple steps:
- Log in into Google Admin Console at admin.google.com (Sign in using an administrator account)
- In the Admin console, go to partyIdP.
- Check the ‘Set up single sign-on (SSO) with a third party IdP’box.
- (AuthN Portal action) Copy the value of the ‘Sign-in page URL’ from AuthN Portal....and paste it into ‘Sign-in page URL’ field.
For ‘Sign-outpage URL’, put anything e.g. https://www.google.com - Download IdP Certificate from the AuthN Portal ...and upload it by selecting ‘Replace certificate’ (this option might be called differently if the cert has never been uploaded)
- Check the ‘Use a domain specific issuer’ box.
- On AuthN Portal, for the Domain field, enter the Primary Domain from the Google Admin Console.
- Click Save.
For further documentation on all other options available, consult Google’s support pages on how to integrate Google Workspace with a third party IdP.
Supported Google Workspace Services
Everything within your account is protected:
Google Admin
Gmail (Email)
Google Drive
Google Calendar
Google Docs, Sheets & Slides
Google Forms
Google Sites
Google Meet & Google Chat
And everything
else that is available beyond your login….

And yes, we also protect any legacy password-based systems.
AuthN by IDEE seamlessly integrates with Google Workspace through modern federation protocols. Thereafter, any application can be seamlessly accessed via MFA 2.0.
In addressing the needs of legacy systems reliant on passwords, AuthN by IDEE offers seamless integration with reverse proxy, Zero Trust Network Access (ZTNA), Secure Access Service Edge (SASE) and Virtual Private Network (VPN) solutions. By enforcing phish-proof Multi-Factor Authentication (MFA 2.0) prior to password entry, AuthN ensures robust security measures are in place. This approach guarantees that only authenticated users that have the appropriate access rights to the designated application, and that have successfully completed the MFA 2.0 process, are permitted to enter passwords and gain access, thereby fortifying system security comprehensively.
.avif)

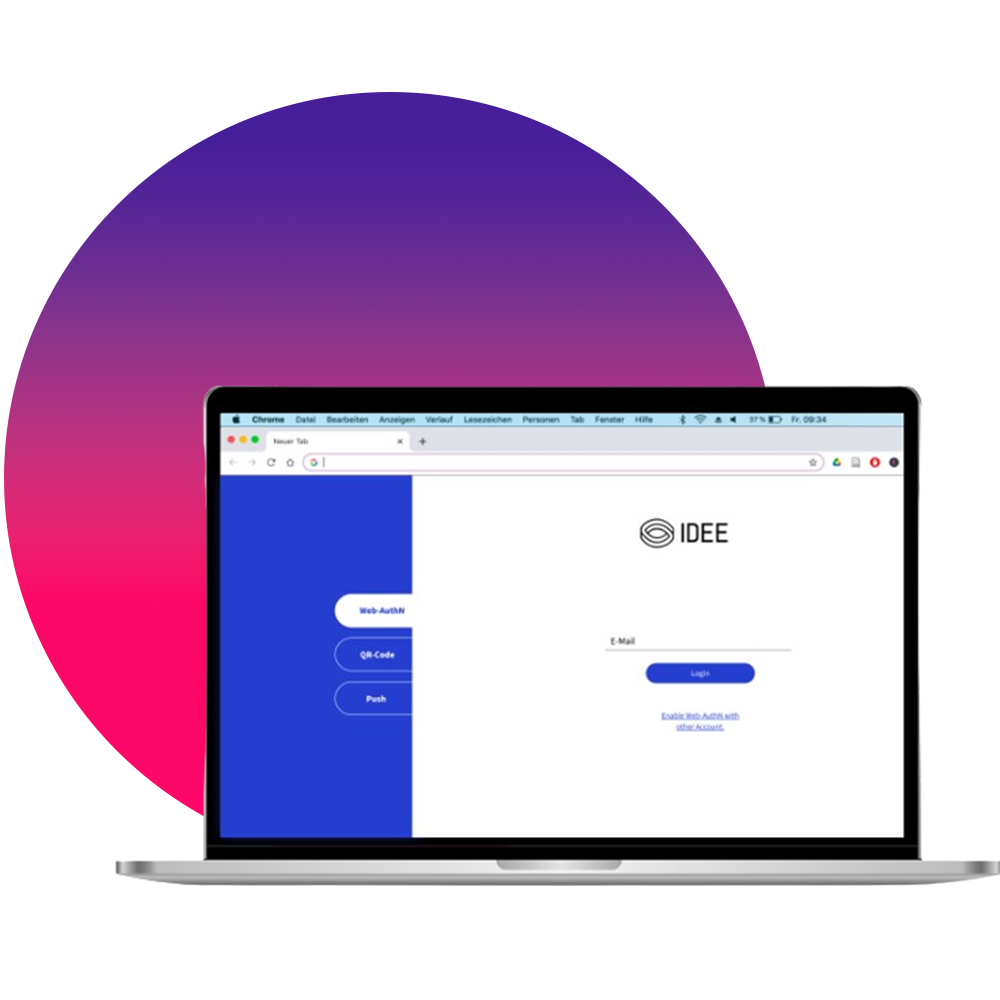
Chose An Authentication Method That’s Right for You
We highly recommend you use WebAuthn which is the phish-proof, friction-free, same-device MFA 2.0 method. However, you do have choices and, it is up to you. Supported authentication methods include:
- WebAuthn
- FIDO2 Security Key
- PUSH
- QR
Web-Authn offers the highest level of protection. We ensure that your digital identity is secure from phishing and password-based attacks throughout the entire lifecycle, which is why Web-Authn is our preferred and recommended option.
Device Requirements
Web-Authn works on any computer with a TPM chip (most machines from 2016 onwards have this) and/or any smartphone with a secure enclave or secure element is also compatible.
The following popular browsers are supported:
- Microsoft Edge
- Chrome
- Safari
- Internet Explorer 7 or higher
User Enrolment
Register A New Device in Seconds!
AuthN by IDEE ensures that only a trusted user can access a trusted service on a trusted device when the user is proven to be in control. User devices, therefore, must be registered. It only takes a few seconds for a user to register their device.
Here’s how it works in just a couple of clicks:
Your Step-by-Step Guide
User goes to Google Workspace for the first time and signs in
They will be redirected to AuthN by IDEE to set up their device.
The user simply unlocks their device, using facial recognition, PIN, Windows Hello, or fingerprint.
They will receive a secure magic link via email.
The user clicks on the link which opens a new tab in the browser.
User clicks ‘accept’ at which point they have registered their device. 🎉
Now every time a user wants to login to their Google Workspace account, they just unlock their device. That’s all.

Fallback Procedures
We don’t just eliminate credential phishing; we also eliminate the stress associated with account recovery!

Never Use a Password Ever Again
(at least not for authentication)!
We don’t like or use passwords because passwords are phishable. We will never ask users to create passwords – not even for account recovery. Be free!
.avif)
No More Phishable Back-up Recovery Methods
Everything you need is already housed within the secure hardware of your registered device. In the unlikely event that you do lose access to your trusted device (which is likely to be your work machine), you simply re-establish trust on your new one using secure identity proofing or setup the new device from an existing device using transitive trust. There is no need to set-up phishable backup Google Authenticator codes or fallback to passwords .. Now that’s a relief!

Reduce Account Recovery
Same-device MFA means no separate keys, or tokens which can be misplaced. Kiss goodbye to expensive hardware replacements and reduce the many reasons to bother IT (hopefully they won’t get lonely)!
Updates & Maintenance
AuthN by IDEE is fully SaaS (Software as a Service). There is nothing to remember to keep up to date to remain secure. With no additional hardware or software of any kind there is no firmware or software to update – you are secure, all the time... Now that’s real peace of mind.
How We Protect Your Data
Actually… what data? AuthN by IDEE holds zero personal identifiable information (PII) about its users, which is one of the reasons why it is so secure! That said, we take security and privacy incredibly seriously. Privacy is our primary company value, and this is why we also go to enormous lengths to ensure we meet all the important standards and compliance regulations you would expect from a chief cyber security vendor.
GDPR Compliant
IDEE is fully GDPR compliant, meaning that we take your data seriously. Always.
ISO 27001
We are 27001 certified.
SOC2 Type II
We are SOC2 certified.
Defense In-Depth
One layer is not enough. We employ layered security for every action.
Decentralized Credentials
Fully decentralized asymmetric keys stored inside the device security chip.
Strong Encryption
AES-256-Bit & ECC-512.
Did Somebody Say Compliance?
Rest assured, we are proud to say, that the AuthN by IDEE technology is backed by all the important standards. Due to new and incoming legislation, this is especially important if you are based in Europe or The United States.
United States - EO 14028 & OMB M-22-09
This executive order outlines the mandate for all federal government agencies and civilian agencies in the federal government, to use phish-resistant MFA. AuthN by IDEE goes one step further, in offering phish-proof protection compliant with EO 14028 & OMB M-22-09.
Europe - The Digital Operational Resilience Act (DORA) - Regulation (EU) 2022/2554 – DORA
DORA is new legislation aimed at increasing security in the financial sector in the EU and asserts that organizations will be obliged to “Implement strong authentication mechanisms, based on relevant standards.” AuthN by IDEE is fully compliant with DORA.
NIST (National Institute of Standards and Technology) Compliant
We are compliant with NIST’s digital identity guidelines (NIST SP 800-63).
FIDO2 Compliant
Expanding upon a FIDO2 compliant architecture, AuthN by IDEE is a strong zero-trust application of MFA. We do not trust blindly; all authentications are explicitly verified.
PSD2 Compliant SCA
Our MFA uses factors that supersede the PSD2 strong customer authentication requirement.
Based on proven Technology
We leverage PKC, TPM/Secure Enclave, and strong encryption.
Transitive Trust
Ensuring a transaction can only be carried out on a “trusted service” by a “trusted device” coupled to a “trusted user” and authorized under the “user’s total control.”
Phish-Proof
Phish-proof > phish-resistant:
AuthN by IDEE protects against every credential phishing and password-based attack, including Adversary in the Middle attacks (AiTM).
Support
It’s easy to find the support you need. Here are your resources:
Admin FAQ
Got questions? Well, the chances are that they may have been asked before, which is why we have a neat collection of the most frequently asked questions all in one place! Check it out!
Raise a ticket
Sometimes we just need a bit of technical support. Do you need to raise a ticket? No problem head over to the service desk and tell us how we can help. We will get back to you quickly!
Report an incident
Is there something we should know about or maybe you just have some excellent feedback for us? Please use this form to report a security incident, vulnerability, or an improvement.
Video tutorials
Already an admin? Visit the Knowledge Centre for step-by-step interactive video tutorials. Looking for demo videos? Check our YouTube playlists.
The IDEE Blog
We discuss many topics on our blog from authentication & cyber security, how our partners can build their business and featured guides and tools. Check it out!
Like what you see?
Speak to us today to try the best MFA solution for yourself.
