Administrator Support
Find answers and help with IDEE's products and services.
Overview
Integration Portal
We require PasswordProtectedTransport in our SAML assertion. Will this work with AuthN by IDEE?
Yes. AuthN by IDEE is passwordless. Nevertheless, to ensure compatability with SAML integrations we enable PasswordProtectedTransport.
How does a new user setup their PC on a Azure AD federated domain when they do not have access to their mailbox?
For new PCs (Out-of-the-box experience) and/or inTune setup, please generate an Access Key from the Integration Portal and provide it to the user so the user can setup their PC.
Where do I find AuthN logs?
AuthN is an IDP. This means that for every integration the logs are provided by the service provider (e.g. Microsoft, Google, Salesforce, etc.). Please refer to the documentation of the service provider to obtain the logs.
What happens to the user's IDEE account when the user's account is deleted from the IAM system or user directory?
Once the user is deleted on your IAM system or from the user directory, the user can no longer log in. To delete the account automatically please leverage SCIM.
Why is it important to setup SCIM between my IAM system or user directory and the Integration Portal?
SCIM ensures that when a user is de-provisioned in the IAM system or user directory, that user is also de-provisioned in AuthN. Once the user is de-provisioned, the user can no longer use AuthN to login.
I cannot change the Immutable ID on my Azure AD federated domain. How do I change the Immutable ID?
Move the user to a new domain (e.g. onmicrosoft.com) change the Immutable ID and then move the user back to the original domain.
What is the admin allowed to do when I invite her to my integrations?
An invited admin is allowed to do the following:
- Edit an integration (modify integration parameters)
- Delete an integration
- View an integration (see integration parameters)
- Invite users
- Delete users from Microsoft or Google integrations
How do I make sure that my shared integrations are not shared with non-priveleged users?
Only the owner of an integration can add/invite another admin.
Does the admin I want to invite to my integrations need to be from the same company?
No, you can invite admins with any email address.
Why am I unable to invite an admin?
Currently , only an existing admin can receive an invitation.
Please make sure that the admin you want to invite is already registered on our Integration Portal.
Can I use the fast integration via your Integration Portal in combination with a branded app?
Yes, you can get a branded setup for your integrations, inlcuding app, login pages, emails, and self-service portal.
Why is my integration not showing on my login screen?
It may take up to 5 minutes for changes to apply. If the integration after 5 minutes is still not taking effect please make sure your integration details are correct.
Why do I need a backup?
A backup allows the admin to add a new device to their account using the backup code. Thereafter, the admin has full access to their account.
I lost my backup code? What do I need to do?
Without a backup code a new device can only be added by proving possession of the mailbox and then resetting your account. Resetting your account means all existing devices are deleted and admin access on the account is revoked. To regain admin access on the account, please submit a support ticket here: https://www.getidee.com/support
How do I login to the Integration Portal?
Go to https://authn.getidee.de and scan the QR-Code with the App. You can either use AuthN by IDEE app or your branded AuthN App from IDEE.
Which authenticator app do I need to download for the Integration Portal login?
You can use the AuthN app or your branded app.
Do I need to register with the same email address in the authenticator app like on Integration Portal?
Yes. In order to use the Integration Portal with your authenticator, you need to use the same email address you used when registering for the Integration Portal with your authenticator. Your email address is your account identifier.
I have an account on the Integration Portal but I cannot access it.
If you recently reset your account, access to your Integration Portal was removed. Please create a ticket here to regain access: https://www.getidee.com/support.
Who should register at the Integration Portal?
The system administrator that is responsible for a specific integration(s) should create an account on the Integration Portal. In order to share an integration with another adminstrator, each adminstrator needs to create an account on the Integration Portal prior to sharing.
Once I have setup my application in the Integration Portal how can I rollout AuthN to all the users?
Once the integration is setup, the user is automatically re-directed to the AuthN login page or the branded login page. On the login page the user is then asked to follow the setps to enable Secure Magic-Link, Web-AuthN or the AuthN app depending on the configuration. Thereafter, the user can instantly login to the application.
When I delete a user on my IAM system (e.g. Microsoft AD), does the user still exist on AuthN?
Once the user is deleted on your IAM system, the user can no longer access any of your systems. Our clients can automatically delete that account on IDEE by leveraging SCIM.
How do I login to the root account of my cloud IAM provider (e.g. Microsoft Azure AD) after I have federated my domain using the Integration Portal?
The root account of your domain cannot be federated. For example, the Microsoft Azure AD root account, onmicrosoft.com, is always accessible by using your username, password, and token.
Who can use the invitation link sent from the Integration Portal?
The invitation link can only be used once by the user who has received the link. The link is tied to the email address that was used when it was created. The user cannot change it.
How do I revert from a federated Microsoft Azure AD domain to a managed domain?
Please use the following command: Set-MsolDomainAuthentication -DomainName $domain -Authentication managed
How do I add a new user to a federated Azure AD only domain?
Once an Azure AD is federated (the integration has been set up), you can begin to add users. Here are the steps:
1. Navigate to your integration in the integration portal.
2. Click on the three dots on the right of the listing to bring up the “Manage Users” menu.
3. Click on “Create user in Azure AD”.
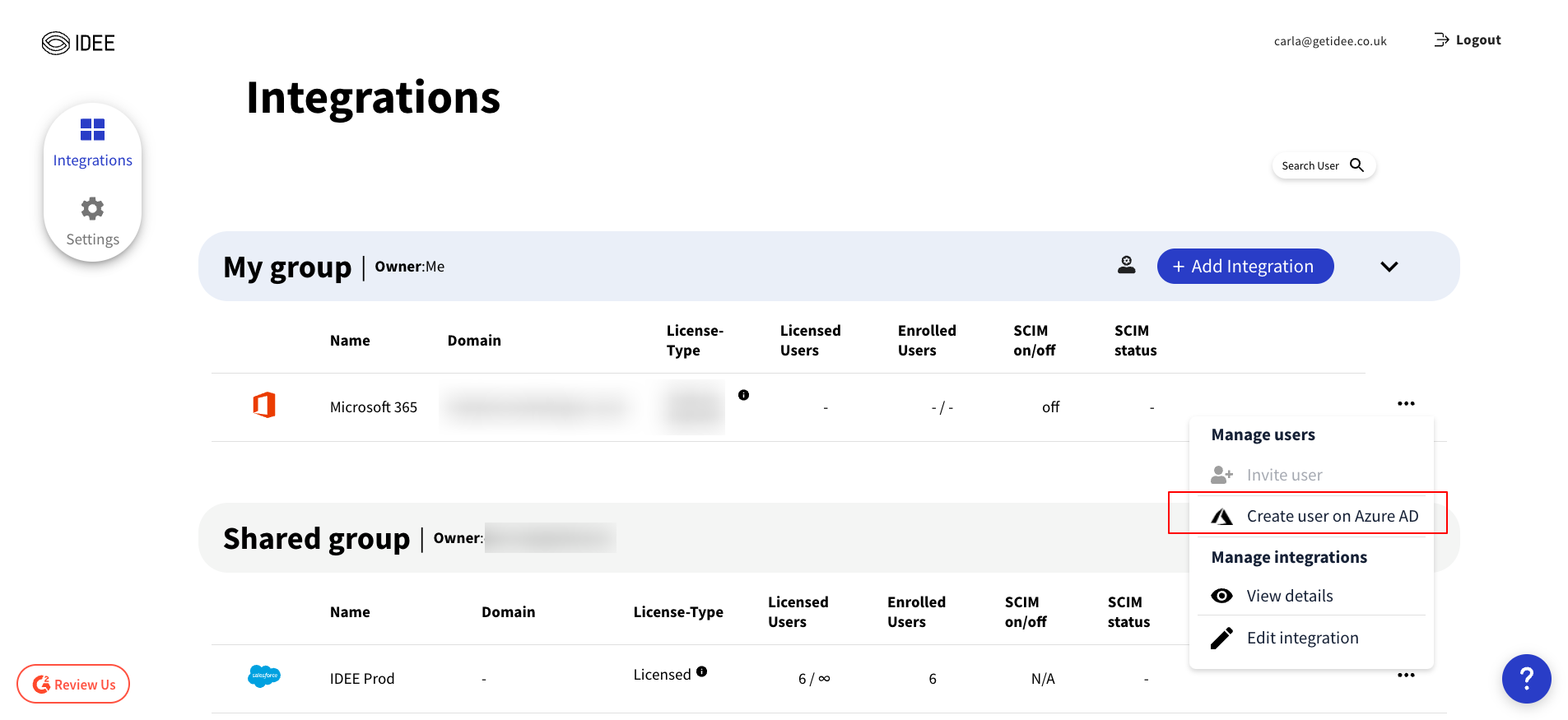
4. Click Grant Access to confirm creating the user
5. Add your user details.
6. Save.
Reporting
How can I report bugs or make feature requests?
Please create a ticket using the "Contact us" button in the right corner below.
Where can I report an incident?
Please create a ticket using the "Contact us" button below choosing the incident section for reports by typing in "incident report".
Device Requirements
What are the device requirements to use AuthN?
The AuthN app works on any smartphone or tablet with the following OS versions:
- Android version 6.0 or higher
- Apple iPhone with IOS 11 or higher
Web-AuthN works on any computer with a TPM chip (internal or external) and the following browsers:
- Microsoft Edge
- Chrome
- Safari
- Internet Explorer 7 or higher
Multiple Account Support
How do I use AuthN with multiple accounts on the same device?
Currently, we support one account per authenticator app. If you choose the branded option, you can use our AuthN app and your branded app. This way you can use two different accounts.
A workaround for Android:Certain phones with Android 10 and later support Dual-apps. With this feature, you can use AuthN in dual-app mode to access two separate mailboxes.
A general workaround: M365 offers delegated access. You can find the M365 documentation here.
With Web-AuthN, multiple accounts can be setup on a single device.
Account Management
After AuthN is enabled, how do I create app passwords for my Microsoft work account?
To enable app passwords on Azure, please enable and enforce Azure MFA. Here is additional information about app passwords.
After I have federated my Microsoft domain, my users are still asked for a username and password login. What should I do?
Once a Microsoft domain is federated, it needs a few minutes to replicate the changes and start redirecting to AuthN login page. Please be patient. Go have a coffee!!
Why am I not allowed to delete my account from Self-service Portal (SSP)?
If your account has active integrations on the Integration Portal you are not allowed to delete your account. You first need to go to the Integration Portal and delete all active integrations or create a ticket to transfer all integrations to another admin. You also need to revoke access to integrations you have shared with other admins. Thereafter, you can delete your account via the Self-service Portal (SSP).
How can I recover my account in the AuthN app when I don't have access to my mailbox?
Please ask an admin who is managing your email integration with AuthN to send you a one-time use magic-link for account recovery. This will allow you to enable your AuthN app as an authenticator. Thereafter you can access your mailbox by using AuthN.
How can I recover my account when I have access to my mailbox but I don't have my backup code?
If you do not have your backup code, you need to reset your account. To obtain access to your integrations on the Integration Portal, please create a ticket here.
What do I do when I have lost my phone, do not have access to my mailbox and do not have my backup code?
Please ask an admin who is managing your email integration with AuthN to send you a one-time use magic-link for account recovery. Therer, you can reset your account and enable AuthN. Once AuthN is enabled, you can authenticate to your mailbox. To obtain access to your integrations on the Integration Portal, please create a ticket here.
What happens when I reset my account?
All authenticator devices are deleted and access to the Integration Portal is removed. You need to contact IDEE to regain access to the Integration Portal. To obtain access to your integrations on the Integration Portal, please create a ticket here.
After AuthN is enabled, how do I manage app passwords for service accounts on Microsoft Azure AD?
App passwords created for service accounts prior to switching the domain from managed to federated will continue to work. If new app passwords need to be created, the admin needs to login to the service account and create new app passwords. When the admin tries to login to a service account, they will need to authenticate with AuthN.
After AuthN is enabled, how do I login to my service account on Microsoft Azure AD?
Please ask an admin to send you a one-time use magic-link to login to your service account using Web-AuthN.
Do I need to disable/delete an enterprise account on IDEE?
Yes. However, once you delete/disable an enterprise account, the user will no longer have access to your data.
User Management
How do I log in as an admin on a user computer after the Azure AD domain is federated?
There are two options.
1) Run powershell and use your admin UPN. If the UPN is part of the federated domain integrated with AuthN, you will be asked to authenticate. Use Push or QR-Code options to authenticate.
2) Log in using the "Other User" option.
You will be asked for a username and password because that is all Windows supports. You can use an admin UPN on the same tenant that ends with onmicrosoft.com suffix or any other UPN, which is part of a managed domain and has admin rights for the federated domain. The UPN must also be listed as a Device Administrator on Azure AD. Here is more info on the device administrator role.
How can I setup users with AuthN and Web-AuthN prior to federating the domain?
You can create the integration on the Integration Portal before federating the domain. Then, a Domain Invite Link will be created. You can send that link to all your users which will enable them to setup a device for that integration before the domain is federated.
I want to enable AuthN for only a subset of users on my Azure AD domain. How do I do that?
You have two Options:
Option 1: To only enable AuthN for a subset of users on a managed Azure AD domain, the admin needs to change the UPN of these users to a federated domain integrated with AuthN. Once complete, the users will login to all Microsoft services using the new UPN and will be required to log in using AuthN.
To change the UPN the admin can go to the user profile in Azure AD and change it or use the following command: Set-AzureADUser -ObjectId <old UPN with managed domain> -UserPrincipalName <new UPN with federated domain>
Option 2: is setting up a subdomain and federating only the subdomain. Follow this guide to set up a subdomain.
How do I add a new user after I federate the domain?
When a domain is federated it is not possible to create users on that domain through Azure Portal.
However, it is possible to create new users using Graph Explorer: https://developer.microsoft.com/en-us/graph/graph-explorer
Sign into Graph Explorer using an Azure admin account, and add required permissions. For managing users User.ReadWrite.All and Directory.ReadWrite.All permissions are required. Please follow these steps:
1. Find and select "create user" sample query.
2. Copy and edit request body from below:
{
"accountEnabled": true,
"displayName": "FirstName LastName",
"mailNickname": "username",
"onPremisesImmutableId": "username@example.com",
"userPrincipalName": "username@example.com",
"mail": "username@example.com",
"givenName": "FirstName",
"surname": "LastName",
"passwordProfile" : {
"forceChangePasswordNextSignIn": true,
"password": "<password>"
}
}
3. Click on "Run query"
What should I do when the user has forgotten their Windows Hello PIN?
If you are on a Hybrid AD domain, first log in using your admin credentials and disconnect the user PC from the domain. Thereafter, re-join the device by asking the user to log in using their AD domain username and password. This will allow the user to setup a new Windows Hello PIN. Once Windows Hello PIN is setup, ask the user to enrol using Web-AuthN again.
After I moved the hard-drive from one PC to another, Windows Hello PIN does not work.
If you are on a Hybrid AD domain, first log in using your admin credentials and disconnect the user PC from the domain. Thereafter, re-join the device by asking the user to log in using their AD domain username and password. This will allow the user to setup a new Windows Hello PIN. Once Windows Hello PIN is setup, ask the user to enrol using Web-AuthN again.
When an account is deleted on my IAM platform (e.g. Microsoft's Active Directory) is that account automatically deleted at IDEE?
No, when an enterprise account is deleted that account needs to be deleted manually on IDEE services (Integration Portal, AuthN User). However, when an account is deleted on your IAM platform, the user no longer can access your data.
To automatically delete the account on IDEE side you need to enable SCIM.
Level 1 Support
Guide on how to do Level 1 Support






You may find your answer in one of the FAQs below or contact us using the form on the bottom of this webpage.
What happens when a user resets her/his account?
All existing devices on that account and any backups are deleted.
How can a user setup an additional device when she enabled one Web-AuthN-device?
The user needs to go to the device that is already setup and start adding an additional device from there.
Why does the user not see the Web-AuthN login option?
On a Windows PC please enable Windows Hello. On a Mac please enable TouchID. On an iOS, iPadOS, Android device please enable system lock.
Web-AuthN option is not available on Safari on a MacMini. Why?
Web-AuthN is available on Safari on a MacMini when using a keyboard with TouchID. Alternatively, the user can use Chrome to have the Web-AuthN option.
How can users recover their account when they don't have access to their mailbox?
User should ask an admin to send them a one-time use magic-link for account recovery. This link will allow them to setup a new authenticator device and thereafter you can access your mailbox.
What is the benefit of creating a backup in the AuthN app?
There are two benefits.
1) A user can add a new device by using the PID (backup code) instead of approving via a push from an existing device.
2) Once a backup is created, a user can only reset their manged account (e.g. M365, Google Workspace) by using an invite link from their adminstrator. A user is unable to reset their account by themselves. This adds addition protection for the user against account take over.
The user did not receive any email with a magic link. How does the user finish enrolling the device?
Please check if the user has entered the correct email. Thereafter, please ensure IDEE is added to your whitelist, so that emails are not stuck in spam or quarantine.
How do I use administrator privileges on a user PC after domain federation?
Once a domain is federated, administrators have two options.
a. If Microsoft modern authentication is available (WebView), authenticate using your administrator account.
b. If Microsoft requires a username and a password, which means modern authentication is not available, use you domain admin username and password if you have an on-premisis AD account or use the onmicrosoft.com admin account if your domain is an Azure AD only domain.
On a HUAWEI P20 Pro, Android version 9, EMUI version 9.1.0 I get a TIMEOUT when I try to login to Microsoft Teams and other Microsoft apps. What do I need to do?
On the phone, go to Settings / Users & accounts / Work account and remove the email you are using to login and try to log in again.
Why does a user get "unable to register" message when he/she tries to register with the AuthN app?
Please ensure that the user has an internet connection. Also ensure that the VPN, firewall, proxy setups are not interfering with access to the IDEE service. Finally, if all else is working please ask the user to disable and enable the lock screen again.
How can a user change his/her account language?
The account language is based on the device language when the account was created and it is automatically set. It cannot be changed.
How can a user change the language in the app?
The app language is based on the device language when the device was added and it is automatically set. It cannot be changed.
Where can users delete/deactivate their device?
Users can delete their device from their Self-Service Portal or from within the authenticator app.
How are multiple accounts supported via Web-AuthN?
On the Web-AuthN login page select Enable Another Account option to setup additional accounts on the same device.
What happens when a user tries to register at IDEE and there is no device lock set?
AuthN does not work without a device lock. Please enable device lock on your tablet, smartphone or computer. For iOS, iPadOS, and Android you need to enable screen lock, for your PC please enable Windows Hello, and for your Mac please enable TouchID.
What happens when a user deletes her device lock after enabling her device as an authenticator?
If you disable device lock on your tablet, smartphone, or computer, AuthN will no longer function. You will have re-enable your device as an authenticator.
What happens when a user resets the account?
All authenticator devices are deleted from the users account. The user can thereafter add devices to his/her account.
How can a users recover their account in the AuthN app when they don't have access to their mailbox?
Users should ask an admin who is managing this email integration with AuthN to send them a one-time use magic-link for account recovery. This will allow them to enable their AuthN app as an authenticator. Thereafter the users can access their mailbox by using AuthN.
Why is there a list of accounts showing when the user tries to login with Web-AuthN?
Probably there are multiple keys for your account stored in the TPM. Here is a guide how to delete them on a Windows PC:
1. Run CMD as administrator → type ‘Command Prompt’ in search bar on Windows, right click and select ‘Run as administrator'
2. In the CMD screen type: certutil -csp NGC -key
This will list all the keys. You’ll see the key in this format: `<sid>/<guid>/FIDO_AUTHENTICATOR// <rpIdHash>_<user id>`
3. Copy the key manually (without the ‘RSA’ at the end), and type in the next command providing the copied key:
certutil -csp NGC -delkey <key>
Press enter.
You should see ‘CertUtil: -delkey command completed successfully’
4. Repeat 3. step for every key.
Here is a guide how to delete them on a Mac:
1. Go to Safari > History
2. Click on Clear History. Please note this will clear all your History in addition to deleting your Web-AuthN keys.
Why does Web-AuthN not show up on Safari iPadOS?
Go to Settings -> Safari -> Request Desktop Website -> All websites.
Why do I not see Web-AuthN as an option in Chrome Incognito mode?
Web-AuthN is currently not supported on Chrome Incognito mode on Windows 10 20H2. It is however supported on MacOS 11.6 and later.
I get a pop-up asking me to insert my security key into the USB port. What should I do?
Click on the cancel button and this will take you to the next window where you need to unlock your PC to authenticate to your website.
The users doesn't see Web-AuthN option on his/her Mac. What should he/she do?
In order to use Web-AuthN on Safari on a Mac, the user must enable TouchID. Please enable TouchID on your Mac and try again.
When the user tries to register an iOS device with Web-AuthN, the user is stuck after he/she unlocks the device. What should the user do?
Click outside of the pop-up and you will get an error, "Something went wrong. Please try again." Now click on login and unlock your phone to authenticate to the website. This is a known bug on iOS and it has been reported to Apple.
When the user tries to register an iPadOS device with Web-AuthN, the user is stuck after he/she unlocks the device. What should the user do?
Switch to another app and go back to Safari and you will get an error, "Something went wrong. Please try again." Now click on login and unlock your phone to authenticate to the website. This is a known bug on iPadOS and it has been reported to Apple.
What happens when the users phone is offline?
No problem. We offer offline login.
